If I was using Server 2003 or 2008 on my domain controllers I’d need to update the schema to support Windows 8 or newer.
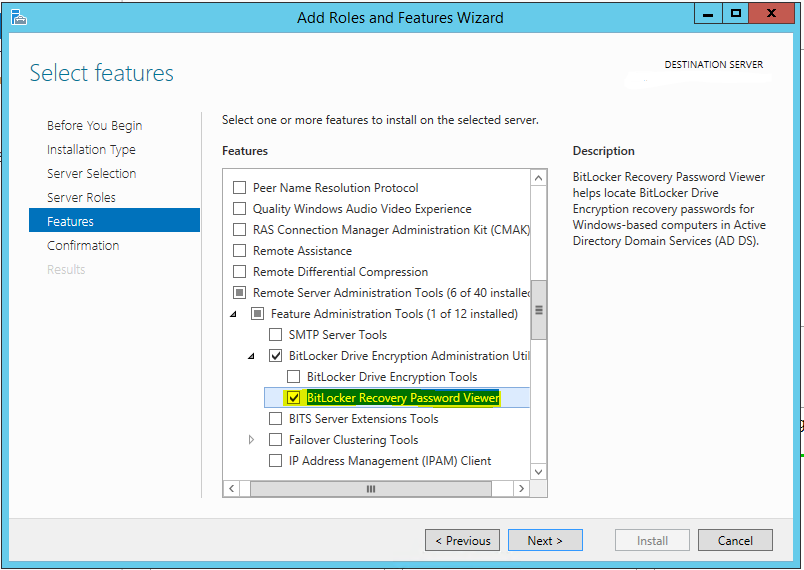
Make sure you have the Bitlocker Recovery Password viewer installed on a server somewhere (unfortunately this cannot be installed on a workstation at this time)
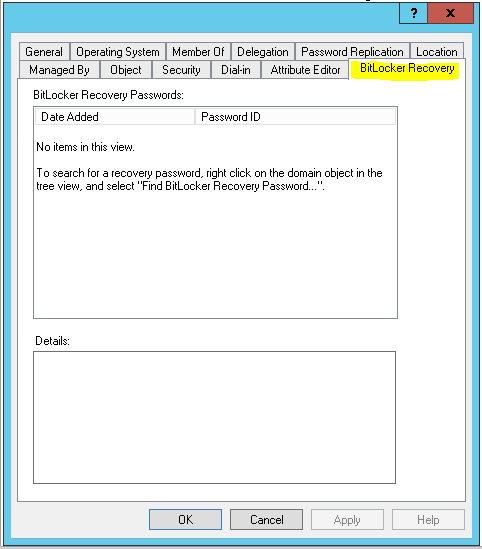
When looking at a Computer object in active directory you should now see a tab for Bitlocker Recovery
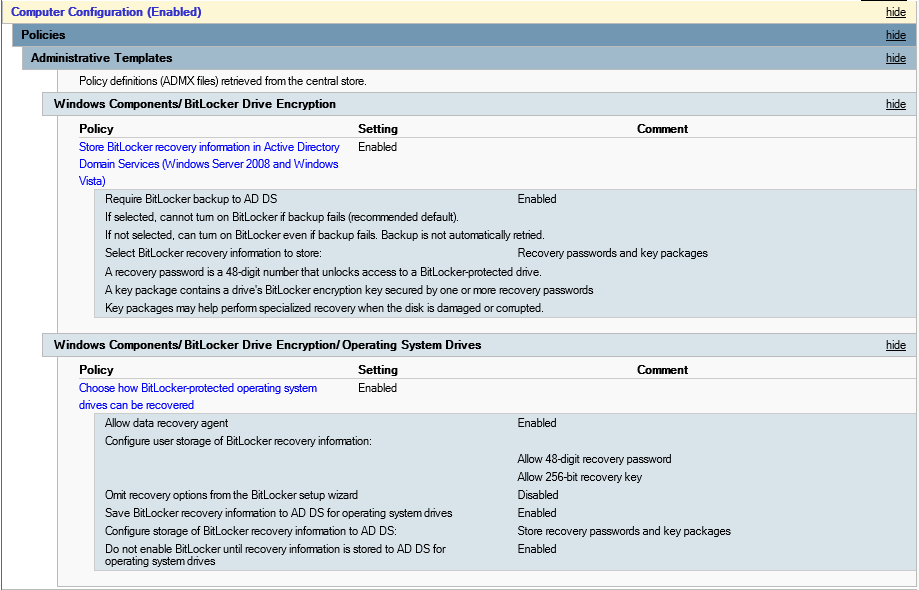
Setup Group Policy to store keys in Active Directory. (If this isn’t set nothing will be stored in Active Directory even if you try to force the password to be stored in Active Directory)
Make sure the PC got the policy, I ran gpresult on a few computers to make sure the policy had come down.
Then encrypt the PC.
If you have computers that are already encrypted with bitlocker you can manually push the key to Active Directory by using the following commands.
First run
manage-bde -protectors -get C:
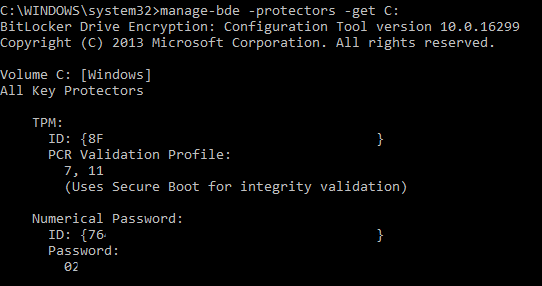
This should give you a ID, make sure to use the ID for the Numerical Password.
manage-bde -protectors -adbackup C: -id {xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}
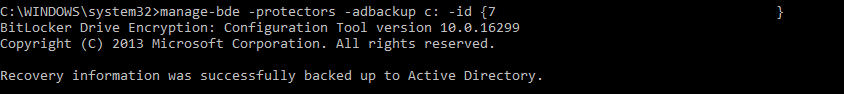
If everything was successful you should now be able to check in Active Directory Users and Computers and look up the computer this was run on and see a recovery password in the BitLocker Recovery Tab.
For doing this remotely you can use the following commands
manage-bde -protectors -get -computername computernamehere C:
Then run
manage-bde -protectors -adbackup -computername computernamehere C: -id {xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}

