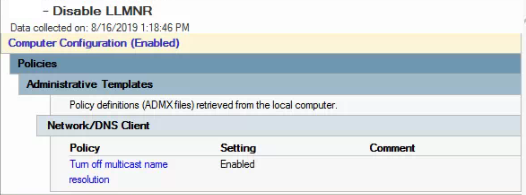
- Disable LLMNR via GPO
- Startup Script to disable NetBios
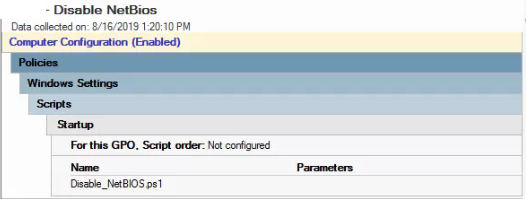
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey |foreach { Set-ItemProperty -Path "$regkey\$($_.pschildname)" -Name NetbiosOptions -Value 2 -Verbose}
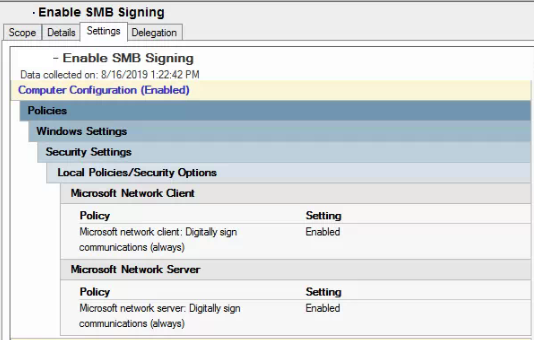
- Enable SMB Signing (Test this with a small batch of computers and note that it won’t take effect until a reboot. Should encounter any issues unless they have older systems like Vista and 2003. Here is the reference article: https://blogs.technet.microsoft.com/josebda/2010/12/01/the-basics-of-smb-signing-covering-both-smb1-and-smb2/)
- Add DNS Entry
- Check block list: dnscmd /info /GlobalQueryBlockList
- remove wapd and make sure isatap is still in the list: dnscmd /config /GlobalQueryBlockList isatap
- Created DNS A record for wpad pointing to the internal IP address of the sonicwall firewall
- Create Sonicwall rule to drop wpad request
- Navigate to Firewall | Match Objects and click on “Add New Match Object”.
- Set Match Object Type to “Custom”.
- Match type : exact match
- Content wpad.dat
- Navigate to Firewall | App Rules.
- Create an app rule using the match object to drop the connection




